Setting up Encryption
Back at the main partitioning screen, we need to tell the installer what these logical volumes we just created are going to be used for — namely, encrypted logical volumes.
Select the first volume and press enter.

The partitioner doesn’t know what to do with the volume until we tell it, so select the “use as” section and press enter.
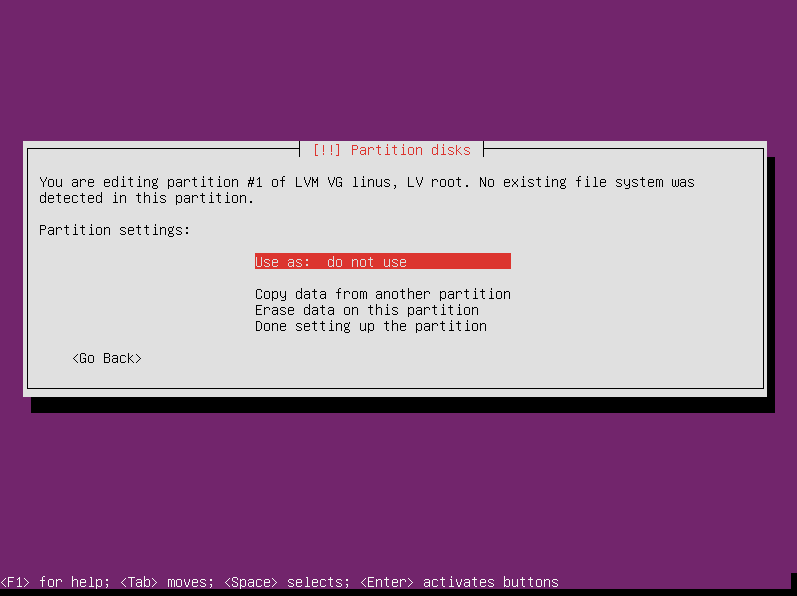
Here we establish that the root filesystem will be encrypted. Choose “Physical partition for encryption” and press enter.

The partition settings screen now shows several encryption-specific options, but we don’t need to change anything because all the defaults are how we want them. Select “Done setting up the partition” and press enter.
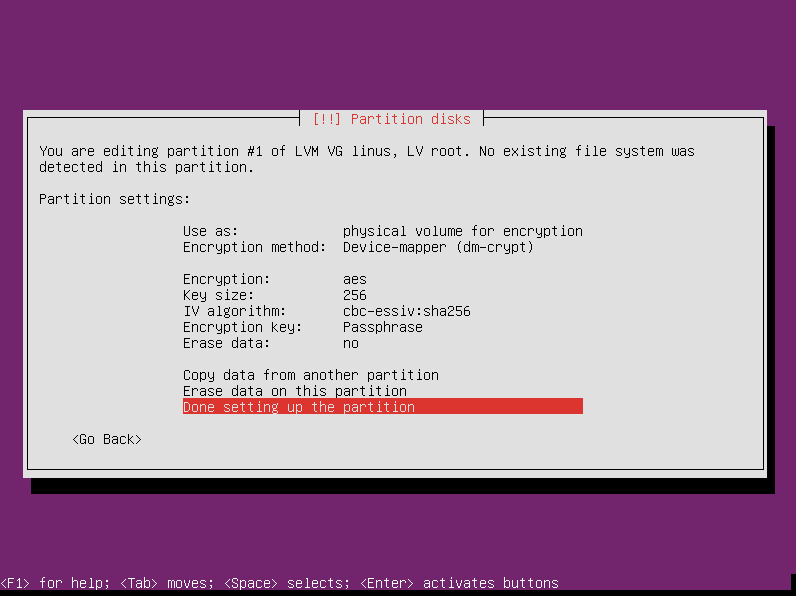
Now we do the same thing for the second volume. Select it from the main partitioning window and press enter.

Again, by default the system doesn’t know what to do with it, so select the “use as” section so we can enlighten the installer.

This volume will also be encrypted, so select “Physical volume for encryption” and press enter.

The encryption options will be mostly correct, but instead of using a passphrase for this volume, we’re going to use a random key. This is because this area is going to be used for swap space. Swap space is not persistent across reboots, so it doesn’t need to be unlocked with the same key. It can be decrypted with a random key that is only valid for that boot. On the next boot, the system will generate a new key and write over the swap space.
The benefit for you is that you only have to enter one passphrase — the one for the root filesystem — instead of two.
To change this, select “Encryption key” and press enter.
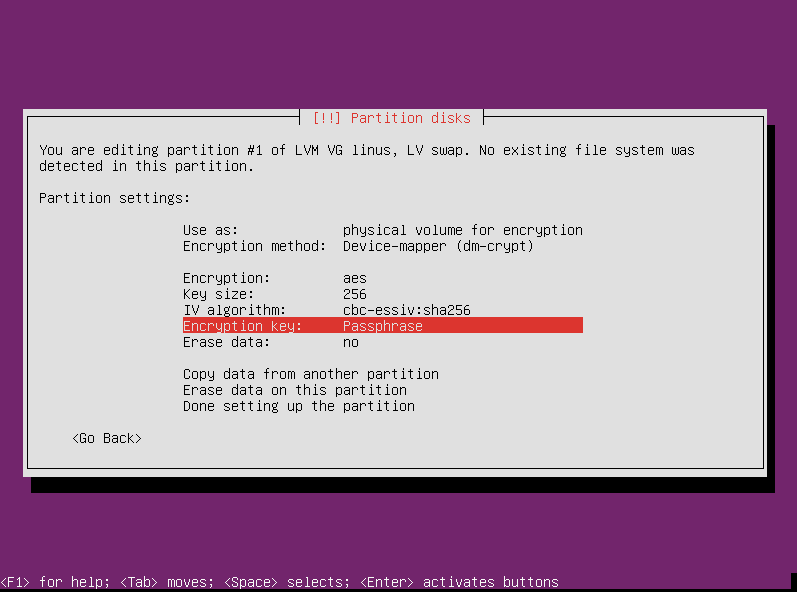
Then select “Random Key” and press enter.

Select “Done setting up the partition and press enter.”
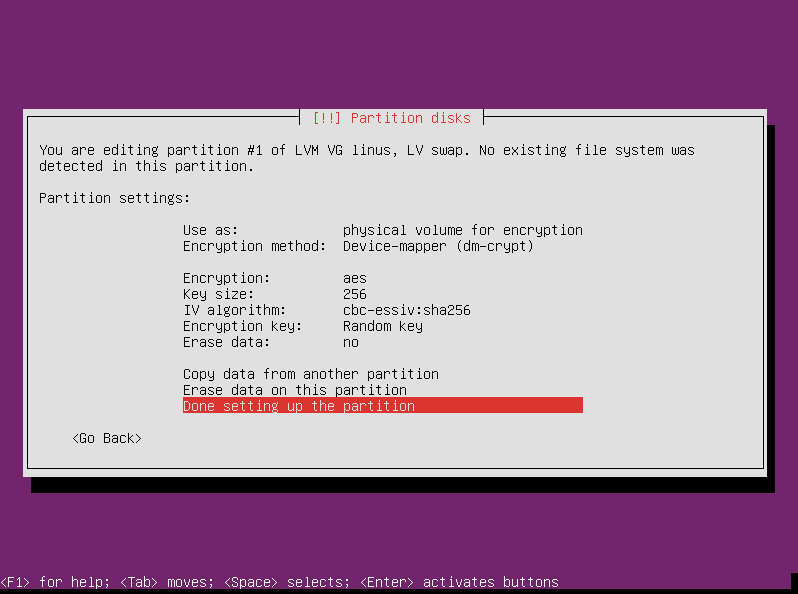
Back at the main partitioning screen, select “Configure encrypted volumes” and press enter.

The partitioner warns you that after encrypted volumes are configured, you can’t change them. If you are satisfied with your settings up to this point, select “yes” and press enter.
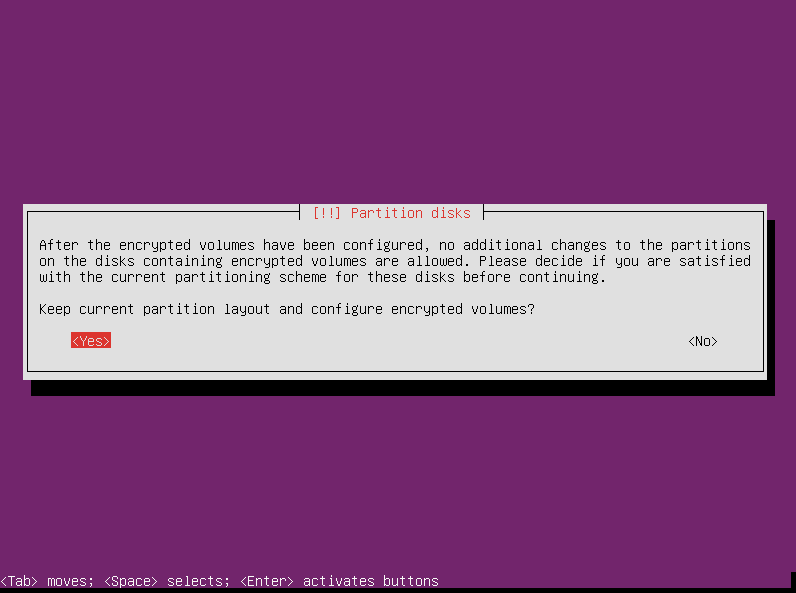
On the next screen, choose “Create encrypted volumes” and press enter.

Select the devices you want to use for encryption with the arrow keys, and mark them with the space bar. Press enter when your chosen devices are marked.
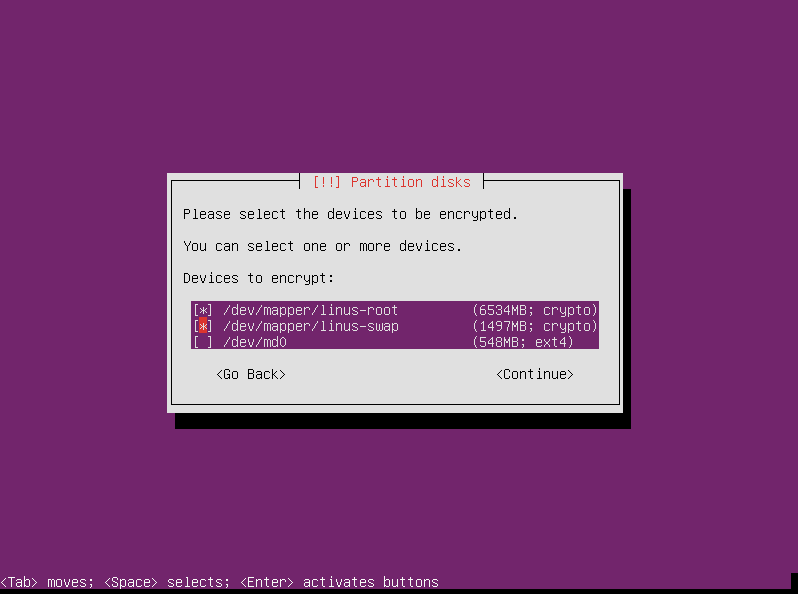
Select “Finish.”

The partitioner now prompts you for your encryption passphrase. This is the passphrase for the root filesystem. It will be needed any time you boot or otherwise access this filesystem.
Enter your passphrase and press enter.
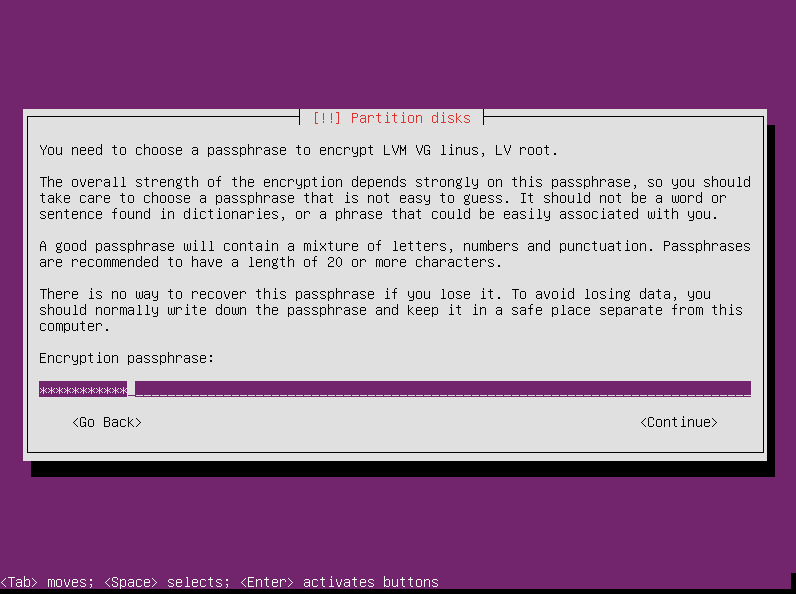
Confirm the passphrase and press enter again.

Back at the main partitioning screen again, it’s time to say what we want to use those encrypted volumes for.
Select the first encrypted volume and press enter.
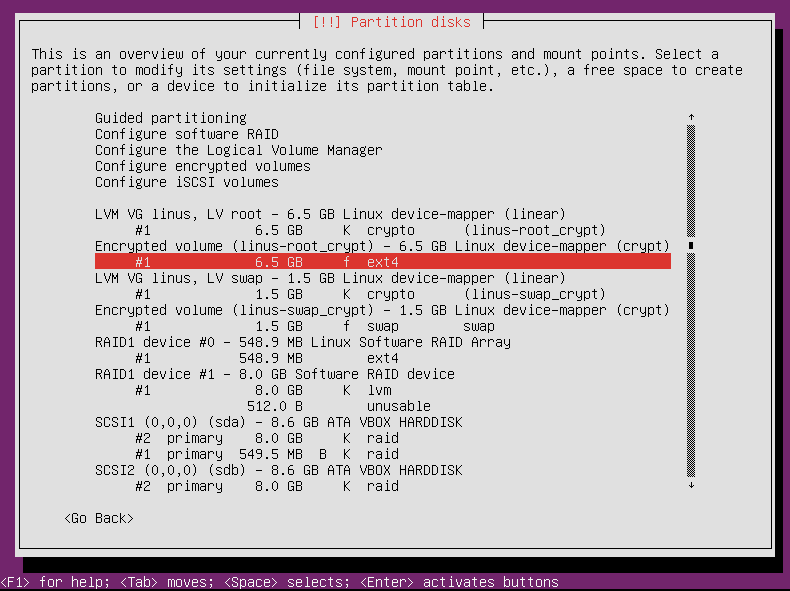
The partitioner defaults to use the volume as an ext4 filesystem. We just need to tell it where to mount it.
Select “Mount point” and press enter.

Select “/ – the root filesystem” and press enter.
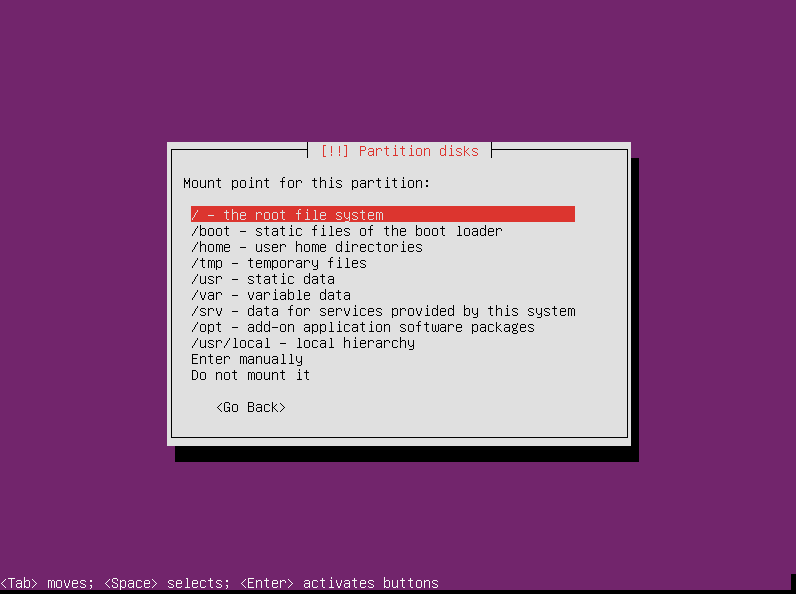
That’s all we need to do here. Select “Done setting up the partition” and press enter.

When you return to the main partitioning screen, you can see the second encrypted volume is already set to be used as swap, so you don’t need to even bother going into the partitioning editing section for this volume.
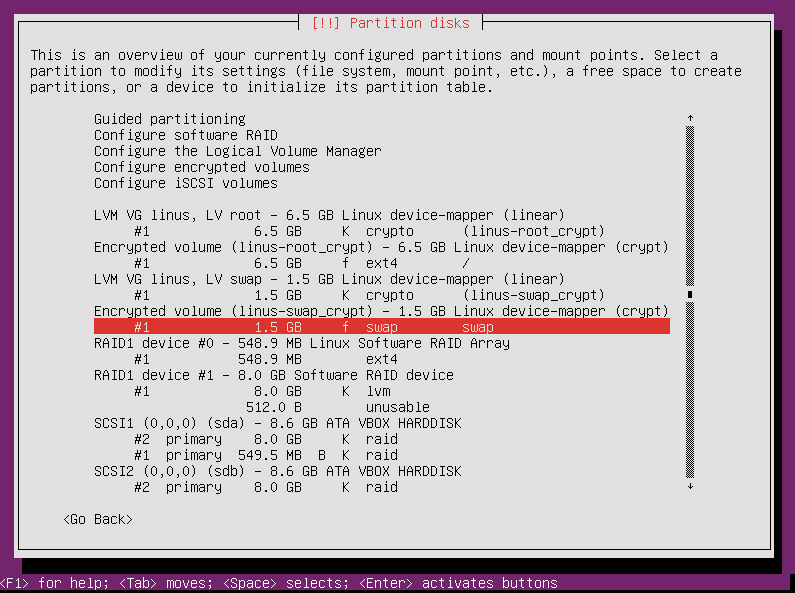
But if you do decide to go in to make sure, this is what you should see (and if this isn’t what you see, this is what you should set it to).

Tying up any Partitioning Loose Ends
Before we move on with the rest of the installation, we just need to configure the boot partition.
Select it from the main partitioning screen and press enter.
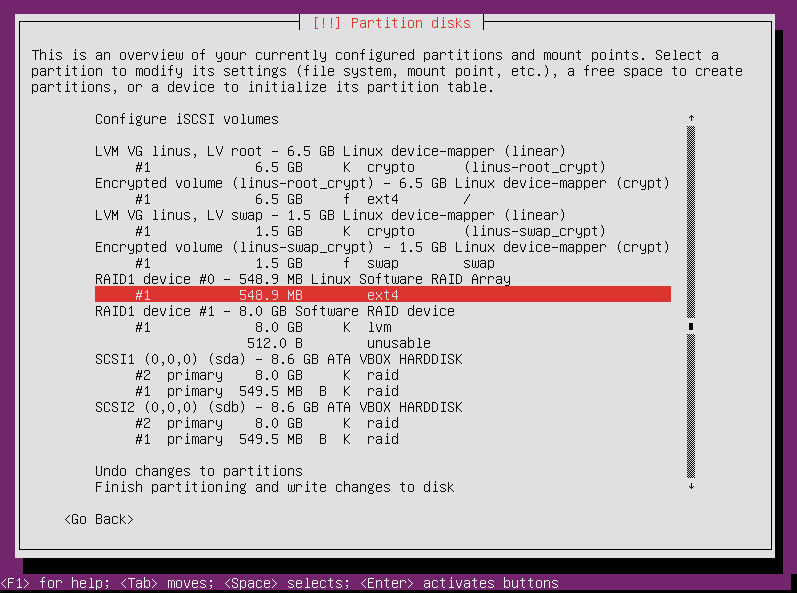
Select “use as” and press enter.

Choose the filesystem type you want to use for your boot partition. I’m sticking with ext4. Press enter after you make your selection.
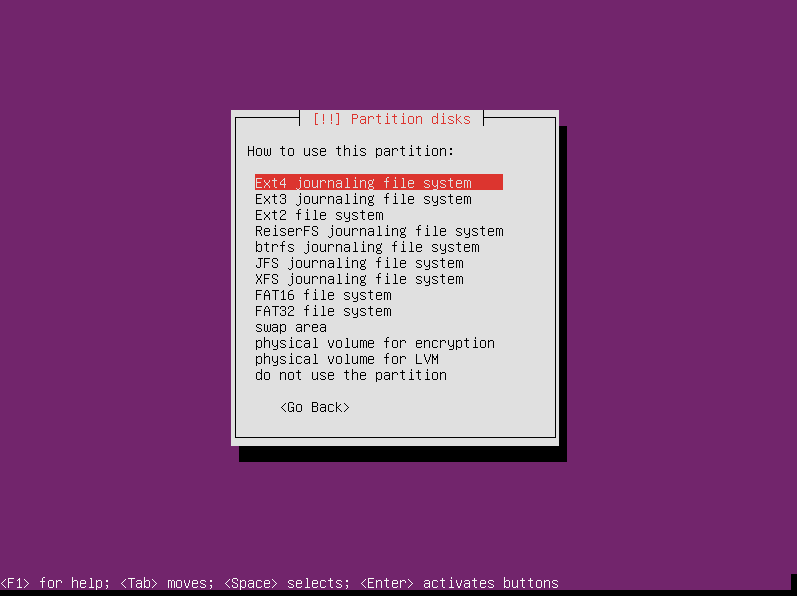
Select “Mount point” and press enter.

Select “/boot — static files of the bootloader” and press enter.
Select “Done setting up the partition” and press enter.

Now with the new installers the bootable flag cannot be set to on for the raid partitions which means you cannot configure raid 🙁 Moreover the boot now is by default set to EFIboot which complicates things even better. The combination of raid 1 and lvm is critical for professional environments. This is a great tutorial. Could you update it? That would be awesome. Thanks!
I’m not sure what you mean by “the new installers.”
he means the installers from 14.04 – these changed many things…
Thank you — this was extremely helpful!!
Hey, Jonathan! Glad to hear it helped.
Great tutorial. Thanks for taking the time to do this.
Thanks, Gary. Glad to help.
I am having a problem with this setup. If I unplug either drive, the system will not boot. I get the error message: “Begin: Waiting for encrypted source device……”. So far I have not been able to find any help on what the solution to this is.
Thank you,
Gary
The instructions here are very clear and helpful. BUT I built it with Ubuntu Server 14.04.1 and have the same problem as Gary – if I unplug either drive and boot, the system says “no volume groups found … waiting for encrypted source device”
I then rebuilt with RAID->LUKS->LVM rather than RAID->LVM->LUKS but get exactly the same problem.
Lst time I tried this (in 2010) the same problem cropped up. I really don’t think Ubuntu has paid much attention to the need for encrypted RAID to work.
I even tried putting a clean disk in place of the “removed” disk to see if it rebuilt, but still says just “waiting for encrypted source device”.
I gave up on Ubuntu for this. Instead I installed a minimal version of Debian 6.0.10 and the encrypted RAID works perfectly; that is removing either drive still allows you to enter your passphrase and log in.
Seems to me there is no point using Ubuntu for encryption with RAID if you can’t boot when a drive fails. And since I am about to build a HP microserver for file storage, I do not want to get burnt by a buggy RAID/Encryption setup.
Thanks “the new guy” for the detailed instructions though, they are probably applicable to Debian and maybe other OS’s too.
Hi The New Guy.
I also have “The new installer”, downloaded today and the bugs that George Pligor speaks of are also preventing me from being able to configure a software RAID 1 array on Ubuntu 12.04.3 LTS 64-bit Server.
Some of the changes include:
Not being given a choice to make a partition Primary or Logical.
An added line to give a partition a name
The inability to set the Bootable Flag to “on”.
The bootable flag of course is the killer. It means grub will not instal.
I am unsure why they changed the installer, but I really wish they hadn’t.
I would really like to get my hands on the old installer because the new installer doesn’t recognize a hardware RAID1 array setup in the Intel RAID Utility on my Gigabyte Z87M-D3HP Motherboard either.
OK, so there is no such thing as a “new installer”
turns out the problem was that I was using 3TB HDDs. anything bigger the 2TB and the Partition table needs to be forced to GPT.
The current installer is not able to cope with rives larger than 2TB for RAID.
You need to set the partitions up first in something like GParted (I used GParted Live CD, or you can use Ubuntu Desktop Live DVD and use its GParted.)
explicitly set the Partition table to GPT.
create a partition at least 1.0MB with no file system and set its flag “biosgrub”
create your swap partition and set its flag “raid”
create your main partition and set its flag “raid”
repeat for the other HDD
exit and begin normal instal.
Once you get to the Partitioner, the partitions are already setup, just do the RAID Configuration.
Create MD swap
create MD main
back in the partitioner, choose swap in the array and choose “use as” – swap area
choose the main in the array and choose “use as” – ext4 – mount – / (root)
DONE.
not need to worry about setting bootable flag.
Finish and write changes to disk.
Install will then work.
This is only for HDDs above 2TB that this is necessary.
solution found here:
http://ubuntuforums.org/showthread.php?t=2109438
Thanks for your input, Alan. Those bigger drives pose some interesting challenges.
I read this 2 years later and it’s going to save my day! I had no idea the 2GB limit was a problem, took me forever to start searching and here, of all places my search hits sent me to, at last I find a decent explanation…
Thx a zillion!
This guide was great – thanks for taking the time to prepare!
Hi The New Guy,
Thanks for the effort , the tutorial is clear and very helpful.
I have a question, need advise / help.
With the same setup like the example with a RAID 1 with 2 drives setup , if one of drive is dead and what steps to recover the array after a brand new unformatted hard drive is replaced .
Good documentation like this is priceless thank you for taking the time to write it 🙂 I am interested in Ubuntu administration and will be following this site for future entries
There be any problems with an encrypted partition by adding another PV in LVM? Could you describe the process more?
1) Create new PV (only one drive without MD for simplify): pvcreate /dev/sdc
2) Add PV to VG: vgextend linus /dev/sdc
3) Extend LV: lvextend -LXXX /dev/linus/root
4) Anything with /dev/maper/linux-root_crypt??
5) Resize fs: resize2fs /dev/maper/linux-root_crypt
4) cryptsetup resize…
🙂
Thank You!
This is extremely helpful and easy to follow!
Is not /home missing in this tutorial or is it created automatically within / ?
Awesome tutorial! Thanks a lot!